Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Showing: 401 to 425 of 931Affiliation shown is the affiliation at the time the talk was given.

Whole Genome Sequencing: Innovation Dream or Privacy Nightmare?
Emiliano DeCristofaro - PARC
Protecting Today's Enterprise Systems against Zero-day Attacks
Saurabh Bagchi - Purdue University

I'm not stealing, I'm merely borrowing - Plagiarism in Smartphone App Markets
Rahul Potharaju - Purdue University

Using Probabilistic Generative Models for Ranking Risks of Android Apps
Chris Gates - Purdue University

A Semantic Baseline for Spam Filtering
Christian F. Hempelmann - Texas A&M University-Commerce
Automatic Detection of Protocol Manipulation Attacks in Distributed Systems Implementations
Cristina Nita-Rotaru - Purdue University

Defending Users Against Smartphone Apps: Techniques and Future Directions
William Enck - North Carolina State University
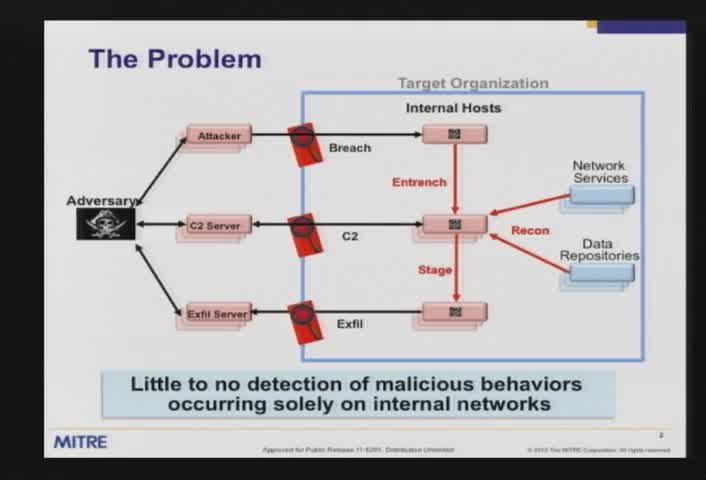
Leveraging internal network traffic to detect malicious activity: Lessons learned
Marc Brooks - MITRE

Global Revocation for the Intersection Collision Warning Safety Application
Jason Haas - Sandia
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List