Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Affiliation shown is the affiliation at the time the talk was given.

Behavioral and Computational Aspects of Network Security Games
Ashish Hota - Purdue University

A2C: Self Destructing Exploit Executions via Input Perturbation
Yonghwi Kwon - Purdue University

CIO Risk Appetite and Information Security Management
Tawei (David) Wang - DePaul University

DataShield: Configurable Data Confidentiality and Integrity
Scott Carr - Purdue University
SymCerts: Practical Symbolic Execution For Exposing Noncompliance in X.509 Certificate Validation Implementations
Sze Yiu Chau - Purdue University

Pushing Computers to the Edge: Next Generation Security and Privacy Controls for Systems and IoT Devices
Ron Ross - National Institute for Standards and Technology (NIST)

Enabling Trust and Efficiency in Provenance-Aware Systems
Adam Bates - University of Illinois at Urbana-Champaign
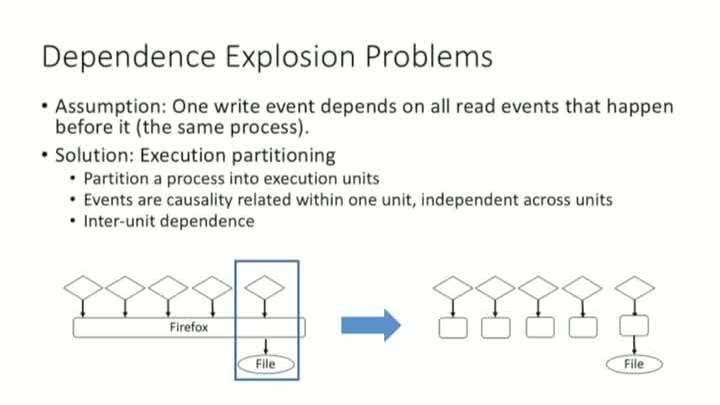
MPI: Multiple Perspective Attack Investigation with Semantic Aware Execution Partitioning
Shiqing Ma - Purdue University

The Stark Reality of Red vs. Blue and Why it's Not Working
Chris Roberts - Acalvio Technologies

Locally Differential Private Protocols for Frequency Estimation
Tianhao Wang - Purdue University

Applying commercial best practices to DoD risk management to offer suggestions how to move from risk avoidance to cost effective risk management
Jerome Edge - Lockheed Martin

Refraction Networking: Censorship Circumvention in the Core of the Internet
Nikita Borisov - University of Illinois at Urbana-Champaign

Securing the Future of Business: Broadening the Role of Security Technology
Kirsten Bay - Cyber adAPT
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List


















