Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Affiliation shown is the affiliation at the time the talk was given.
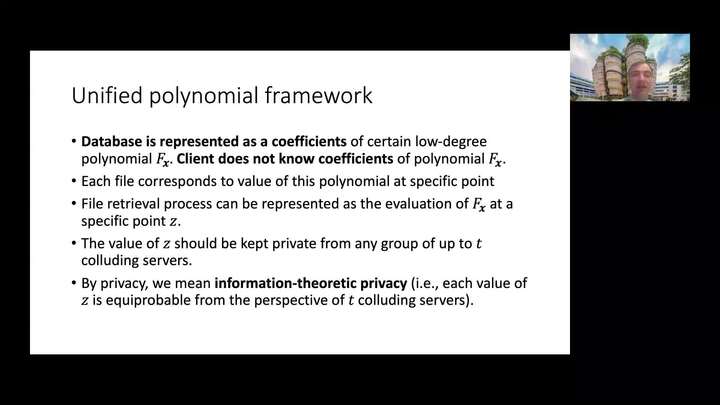
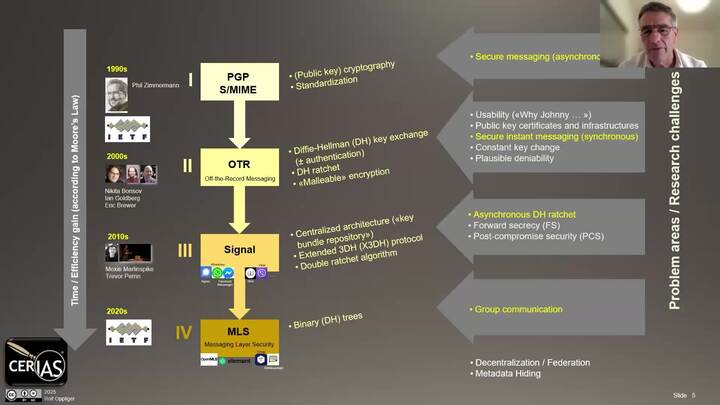
Querying Twice: How to Ensure We Obtain the Correct File in a Private Information Retrieval Protocol
Stanislav Kruglik - NTU Singapore
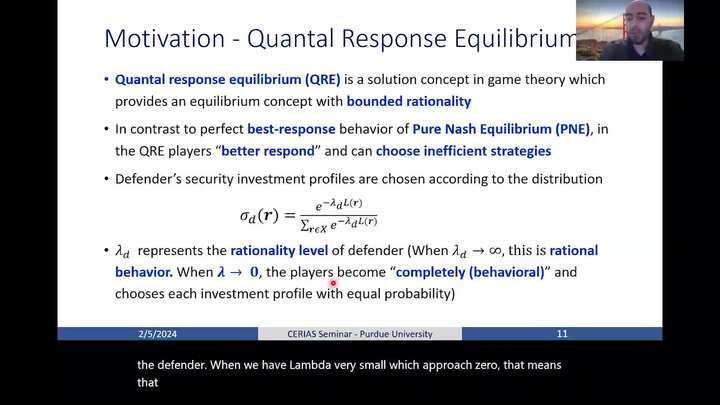
Effects of Behavioral Decision-Making in Proactive Security Frameworks in Networked Systems
Mustafa Abdallah - Purdue University in Indianapolis
Measuring Data Protection: A Causal Artificial Intelligence Modeling Approach
Robert Morton - Google Cloud

Zero Trust Architectures and Digital Trust Frameworks: A Complementary or Contradictory Relationship?
Ali Al-Haj - Princess Sumaya University for Technology
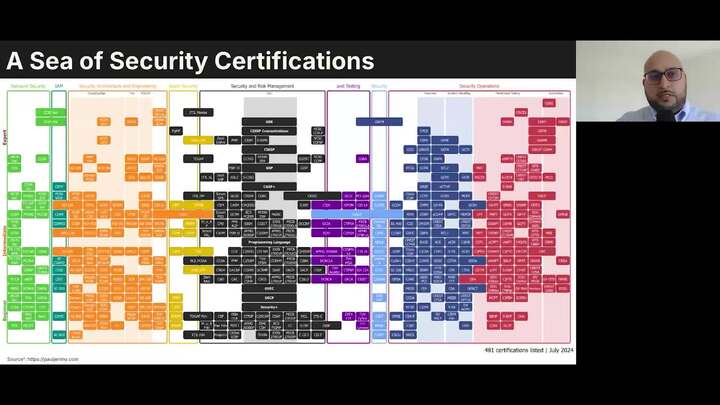
Decrypting the Impact of Professional Certifications in Cybersecurity Careers
Hisham Zahid & David Haddad
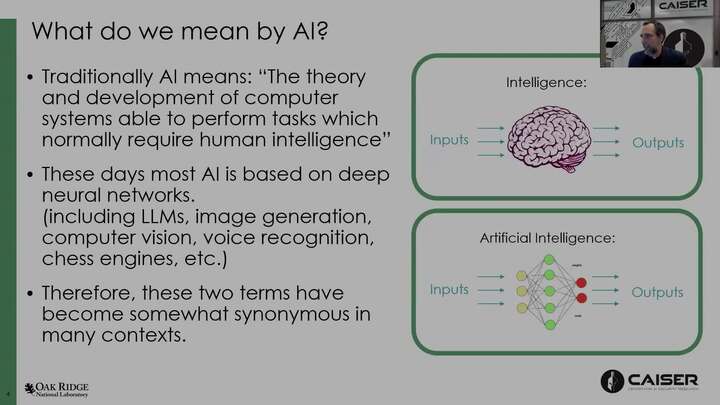
What do we mean when we talk about AI Safety and Security?
Amir Sadovnik - Oak Ridge National Laboratory

Annual CERIAS Security Symposium Closing Keynote IT, OT, IoT — It's Really Just the "T": An International and Historical Perspective
Michael Clothier - Northrop Grumman

Lessons for Cybersecurity from the American Public Health System
Josiah Dykstra - Trail of Bits
Russian Hacking: Why, How, Who, and to What End
Richard Love - National Defense University
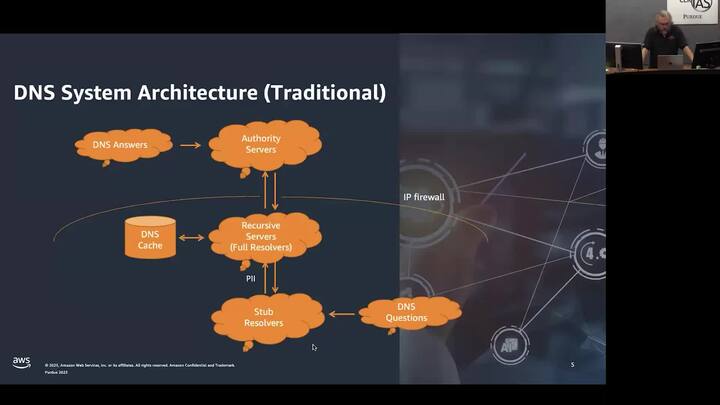
Force Projection in the Information Domain: Implications of DNS Security
Paul Vixie - Amazon Web Services (AWS)

Utilization of National Guard Cyber Forces in Title 32 Status for National Cyber Missions
Dave Schroeder - University of Wisconsin-Madison
The Converged Threat Landscape: What's Next in Cybersecurity
Kris Lovejoy - Kyndryl Global Security

Securing Linux in a Heterogenous Enterprise Environment
Matthew Sharp - Toyota Motor North America

The Shape of Trust: Structure, Stability, and the Science of Unlearning
Rajiv Khanna - Purdue University

Malware Detection under Concept Drift: Science and Engineering
Marcus Botacin - Texas A&M

When is Automatic Privacy Proof Possible for Black-Box Processing?
Hanshen Xiao - Purdue University

The Hidden Laundromat at Play: how illicit value moves through online games
Stephen Flowerday - Augusta University

From MOVEit to EBS – a Look at Mass Exploitation Extortion Campaigns
Peter Ukhanov - Google Public Sector (Mandiant)
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List