Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Affiliation shown is the affiliation at the time the talk was given.

Is it Time to add Trust to the Future Internet/Web?
George Vanecek - Futurewei Technologies

Digital Citizenship: A Target's View of Security and Life Online
Kelley Misata - PhD Candidate, Purdue University
Forensic Carving of Network Packets with bulk_extractor and tcpflow
Simson Garfinkel - Naval Postgraduate School

Cryptographic Protocols in the Era of Cloud Computing
Nishanth Chandran - Microsoft Research

Privacy-Preserving Assessment of Location Data Trustworthiness
Chenyun Dai - Purdue University

Adding a Software Assurance Dimension to Supply Chain Practices
Randall Brooks - Raytheon
Privacy preserving attribute based group key management
Nabeel Mohamed - PhD Candidate, Purdue University

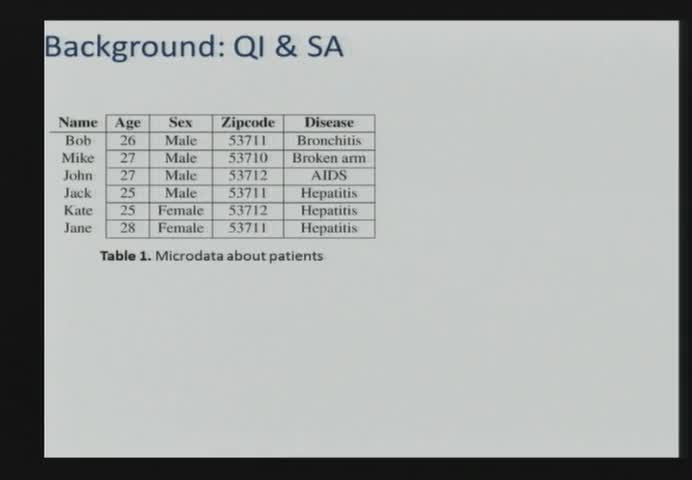
: K-Anonymity in Social Networks: A Clustering Approach
Traian Truta - Northern Kentucky University

What firmware exists in your computer and how the fight for your systems will be below your operating system
Steve Battista - MITRE

Global Revocation for the Intersection Collision Warning Safety Application
Jason Haas - Sandia
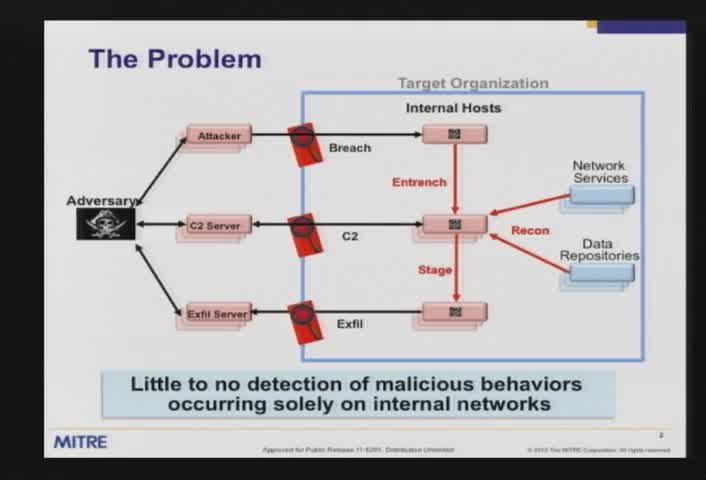
Leveraging internal network traffic to detect malicious activity: Lessons learned
Marc Brooks - MITRE

Defending Users Against Smartphone Apps: Techniques and Future Directions
William Enck - North Carolina State University
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List