Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Affiliation shown is the affiliation at the time the talk was given.
Obfuscated Databases: Definitions and Constructions
Vitaly Shmatikov - University of Texas at Austin
Network Data Streaming - A Computer Scientist's Journey in Signal Processing
Jun Xu - Georgia Tech

Perturbation of Multivariable Public-key Cryptosystems
Jintai Ding - University of Cincinnati
Using process labels to obtain forensic and traceback information
Florian Buchholz - Purdue University
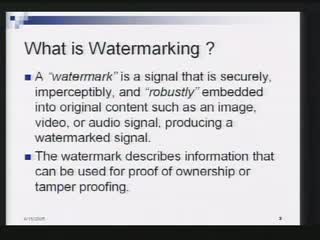
Where's the FEEB? Effectiveness of Instruction Set Randomization
David Evans - University of Virginia

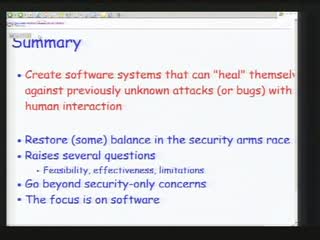
Vulnerability-Driven Network Filters for Preventing Known Vulnerability Attacks
Helen J. Wang - Microsoft Research

Traust and PeerTrust2: Applying Trust Negotiation to Real Systems
Marianne Winslett - University of Illinois at Urbana-Champaign

Minimizing Trust Liabilities in Secure Group Messaging Infrastructures
Himanshu Khurana - University of Illinois at Urbana-Champaign

Toward Hazard Aware Spaces: Knowing Where, When and What Hazards Occur
Peter Bajcsy - University of Illinois at Urbana-Champaign/ National Center for Supercomputing Applications (NCSA)

A Framework for Identifying Compromised Nodes in Sensor Networks
Ting Yu - North Carolina State University
Managing Risk of Information Systems Security Incidents
Dr. Fariborz Farahmand - Purdue University/CERIAS
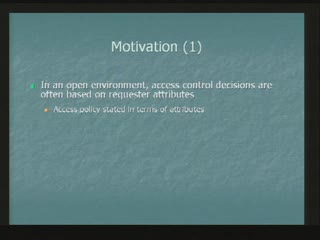
Aligning Privacy Values, Policies, Law and Software Requirements
Annie Anton - North Carolina State University/ Associate Professor and Director, ThePrivacyPlace.Org
The Ontology of Documents and the Technology of Identification
Barry Smith - SUNY Buffalo

Privacy-preserving Policy-driven Access Control with Mixed Credentials
Shouhuai Xu - University of Texas at San Antonio

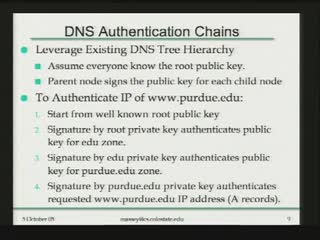
Clouseau: A practical IP spoofing defense through route-based filtering
Jelena Mirkovic - University of Delaware
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List