Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Showing: 1 to 25 of 933Affiliation shown is the affiliation at the time the talk was given.

Discovering and Controlling AI Safety Risks in Foundation Models: A Probabilistic Perspective
Ruqi Zhang - Purdue University

ISO 27001 as the Engine, NIST CSF 2.0 as the Dashboard, A Practical Operating Model
Danny Vukobratovich - Purdue University
Towards Robust and Trustworthy AI Speech Models: What You Read Isn't What You Hear
Thai Le - Indiana University

AI-Assisted Cyber-Physical Attack Detection in Smart Manufacturing Systems
Bethanie Williams - Sandia National Laboratory
Parental Sharing ("Sharenting") Through the Lens of Interdependent Privacy
Mary Jean Amon - Indiana University
Counterfeit Medical Devices and Medicines as a Fundamental Cyber-Physical Security Problem
Young Kim - Purdue University
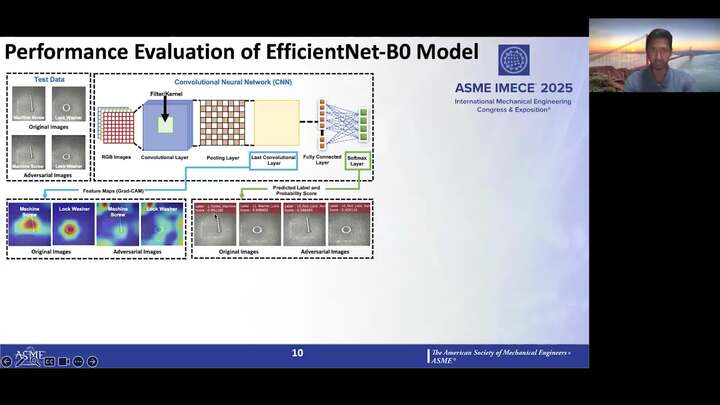
Evaluating The Impact of Cyberattacks On AI-based Machine Vision Systems: A Case Study of Threaded Fasteners
Vijayanth Tummala - Researcher in Cybersecurity and Human-AI Interaction domain
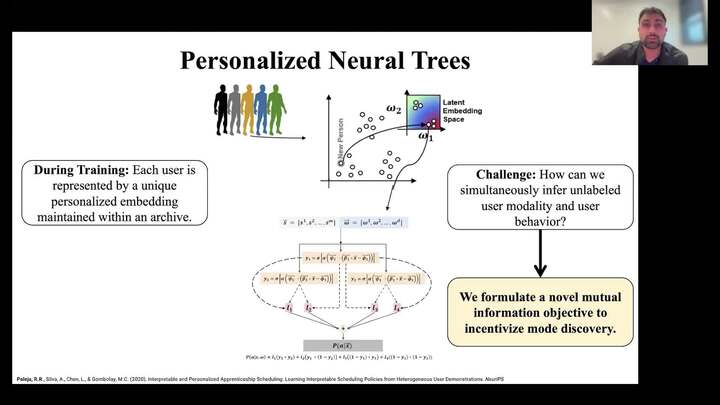
Building Interpretability into Human-Aware Robots through Neural Tree-Based Models
Rohan Paleja - Purdue University

From MOVEit to EBS – a Look at Mass Exploitation Extortion Campaigns
Peter Ukhanov - Google Public Sector (Mandiant)

The Hidden Laundromat at Play: how illicit value moves through online games
Stephen Flowerday - Augusta University

When is Automatic Privacy Proof Possible for Black-Box Processing?
Hanshen Xiao - Purdue University

Malware Detection under Concept Drift: Science and Engineering
Marcus Botacin - Texas A&M

The Shape of Trust: Structure, Stability, and the Science of Unlearning
Rajiv Khanna - Purdue University

Securing Linux in a Heterogenous Enterprise Environment
Matthew Sharp - Toyota Motor North America
The Converged Threat Landscape: What's Next in Cybersecurity
Kris Lovejoy - Kyndryl Global Security

Utilization of National Guard Cyber Forces in Title 32 Status for National Cyber Missions
Dave Schroeder - University of Wisconsin-Madison
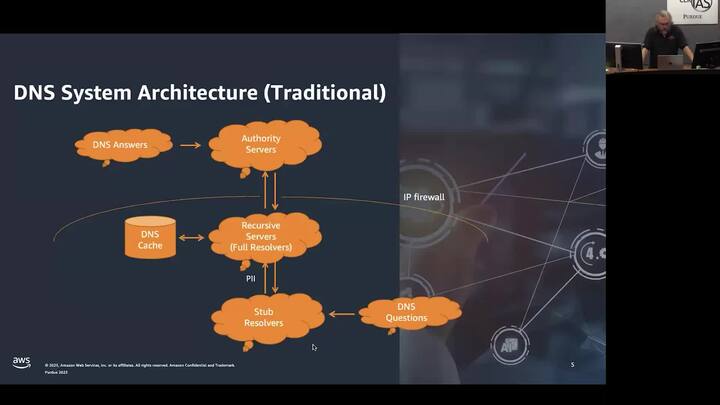
Force Projection in the Information Domain: Implications of DNS Security
Paul Vixie - Amazon Web Services (AWS)
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List