Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Showing: 226 to 250 of 932Affiliation shown is the affiliation at the time the talk was given.

Hardware Cybersecurity Attacks and Some Solutions
Krishna Kavi - University of North Texas

Efficient and Constant-Round Secure Comparison through Function Transformation, Dynamic Group Switching and Asymmetric Computation
Wei Jiang - University of Missouri-Columbia

Securing IoT-based Cyber-Physical Human Systems against diverse attacks
Sathish Kumar - Coastal Carolina University

Game Theoretic Modeling of Cyber Deception in the Internet of Battlefield Things
Charles Kamhoua - US Army Research Laboratory

A Game Theoretic Approach for Adversarial Machine Learning -- When Big Data Meets Cyber Security
Bowei Xi - Purdue University

Protection against Compromised Operating Systems on ARM Cortex-A Architecture
Meng Yu - Roosevelt University
Defending the Grid for Fun and Non-Profit: Cybersecurity and Infrastructure Resilience Research at LLNL
Steve Chapin - Lawrence Livermore National Laboratory

Trustable Information for Security Applications: Visual Analytics for Reliable, Effective Decision Making
David Ebert - Purdue University

Secure Information Forwarding through Fragmentation in Delay- tolerant Networks
Sanjay Madria - Missouri University of Science and Technology
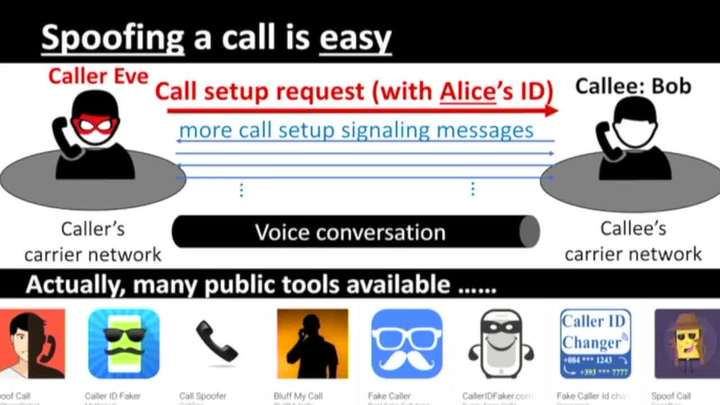
CEIVE: Combating Caller ID Spoofing on 4G Mobile Phones Via Callee-Only Inference & Verification
Haotian Deng - Purdue University

Normalizing Diverse Android Access Control Checks for Inconsistency Detection
Yousra Aafer - Purdue University

Developing a Public/Private Cybersecurity Scorecard for the State of Indiana
James Lerums - Purdue University

Double the Factors, Double the Fails: How Usability Obstacles Impact Adoption of Strong Authentication Habits
Jessy Irwin - Tendermint

Kernel-Supported Cost-Effective Audit Logging for Causality Tracking
Shiqing Ma - Purdue University

What's Private: Exploring Reasonable Expectation of Privacy in the Age of Modern Innovation
Jillean Long Battle - Rofori Corporation

Breaching Water Treatment Plants: Lessons Learned from Complex Exercises
Doug Rapp - Rofori Corporation

Hacking Your Security Career: Strategies That College Did Not Teach Me
Ryan Elkins - Eli Lilly
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List








