Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 | 1970 |
Results
Showing: 426 to 450 of 927Affiliation shown is the affiliation at the time the talk was given.

Adding a Software Assurance Dimension to Supply Chain Practices
Randall Brooks - Raytheon

Privacy-Preserving Assessment of Location Data Trustworthiness
Chenyun Dai - Purdue University

Cryptographic Protocols in the Era of Cloud Computing
Nishanth Chandran - Microsoft Research
Forensic Carving of Network Packets with bulk_extractor and tcpflow
Simson Garfinkel - Naval Postgraduate School

Digital Citizenship: A Target's View of Security and Life Online
Kelley Misata - PhD Candidate, Purdue University

Is it Time to add Trust to the Future Internet/Web?
George Vanecek - Futurewei Technologies

Soundcomber: A Stealthy and Context-Aware Sound Trojan for Smartphones
Apu Kapadia - Indiana University

Jam me if you can: Mitigating the Impact of Inside Jammers
Loukas Lazos - University of Arizona
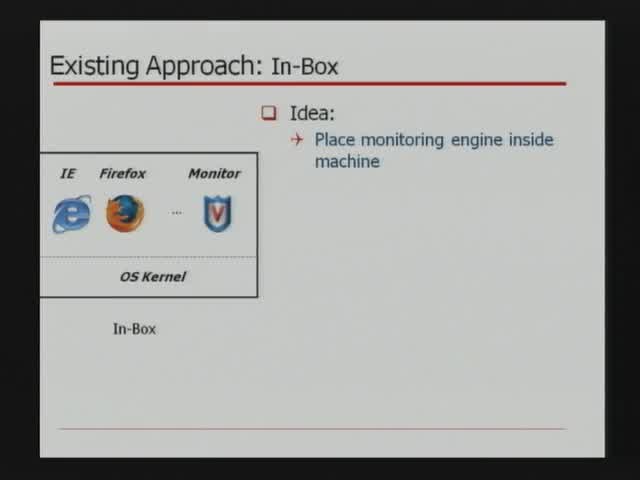
Process Implanting: A New Active Introspection Framework for Virtualization
Zhongshu Gu - Purdue University
SureView AMP, Active Malware Protection, detecting malware anti virus solutions miss
Morgan Greenwood - Raytheon

Securing Application-Level Topology Estimation Networks: Facing the Frog-Boiling Attack
Sheila Becker - University of Luxembourgh

Ontological Semantic Technology Goes Phishing
Julia M. Taylor, Victor Raskin, and Eugene H. Spafford - Purdue University

Enterprise-Wide Intrusions Involving Advanced Threats
Dan McWhorter and Steve Surdu - Mandiant Corporation
Weighted Multiple Secret Sharing
Xukai Zou - Indiana University-Purdue University Indianapolis

Methods and Techniques for Protecting Data in Real Time on the Wire
Joe Leonard - Global Velocity
What does Knowledge Discovery, Predictability, and Human Behavior have to do with Computer Security
David Zage - Sandia National Laboratories
Detecting Bots in Online Games using Human Observational Proofs
Steven Gianvecchio - MITRE
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List