Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Affiliation shown is the affiliation at the time the talk was given.

User and Machine Authentication and Authorization Infrastructure for Distributed Testbeds
Torsten Braun - University of Bern

Understanding insiders: An analysis of risk-taking behavior *
Fariborz Farahmand - Purdue University

Modeling DNS Security: Misconfiguration, Availability, and Visualization
Casey Deccio - Sandia National Labs

Wireless Technologies and how it relates to cyber security research
Kim Trieu - Lockheed Martin
The Threat to Our Nation's Infrastructure and Intellectual Property Is Substantial
Dennis McCallam - Northrop Grumman

Society, Law Enforcement and the Internet: Models for Give and Take
Carter Bullard - QoSient, LLC
FuzzyFusion™, an application architecture for multisource information fusion
Ronda R. Henning - Harris Corporation

Semantic Security: or How I Learned to Stop Worrying and Looooooove the Internet
Jose Fernandez - Montreal Polytechnic
Detecting Bots in Online Games using Human Observational Proofs
Steven Gianvecchio - MITRE
What does Knowledge Discovery, Predictability, and Human Behavior have to do with Computer Security
David Zage - Sandia National Laboratories

Methods and Techniques for Protecting Data in Real Time on the Wire
Joe Leonard - Global Velocity
Weighted Multiple Secret Sharing
Xukai Zou - Indiana University-Purdue University Indianapolis

Enterprise-Wide Intrusions Involving Advanced Threats
Dan McWhorter and Steve Surdu - Mandiant Corporation

Ontological Semantic Technology Goes Phishing
Julia M. Taylor, Victor Raskin, and Eugene H. Spafford - Purdue University

Securing Application-Level Topology Estimation Networks: Facing the Frog-Boiling Attack
Sheila Becker - University of Luxembourgh
SureView AMP, Active Malware Protection, detecting malware anti virus solutions miss
Morgan Greenwood - Raytheon
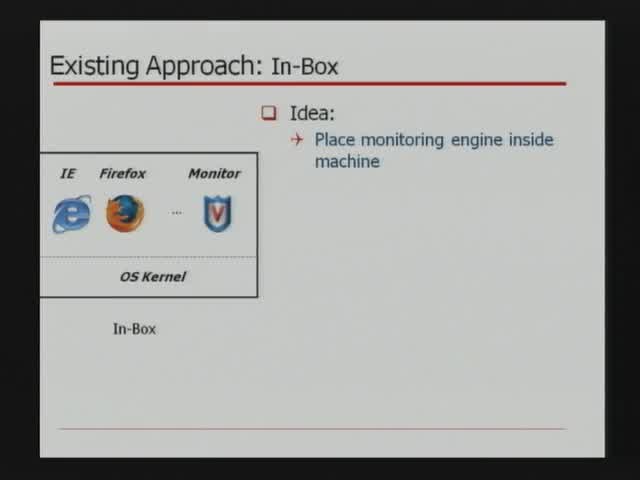
Process Implanting: A New Active Introspection Framework for Virtualization
Zhongshu Gu - Purdue University

Jam me if you can: Mitigating the Impact of Inside Jammers
Loukas Lazos - University of Arizona

Soundcomber: A Stealthy and Context-Aware Sound Trojan for Smartphones
Apu Kapadia - Indiana University
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List