Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Showing: 151 to 175 of 931Affiliation shown is the affiliation at the time the talk was given.

Security Engineering for Machine Learning
Gary McGraw - Berryville Institute of Machine Learning

Cybersecurity Skills – Easy to say, harder to recognise?
Steven Furnell - University of Nottingham in the United Kingdom
Delving into differential privacy and anomaly detection: a meta-learning perspective
Yimin Chen - Virginia Tech
The Invisible Risks: An Empirical Analysis on Data Sharing Activities and Systemic Risk among the Data Brokers
Tawei (David) Wang - DePaul University
Practical software Supply Chain Security and Transparency
Santiago Torres-Arias - Purdue University

SDN/NFV in the ICS, SCADA and Manufacturing World as a Cyber Security Tool
Greg Akers - Executive Technology Consultant
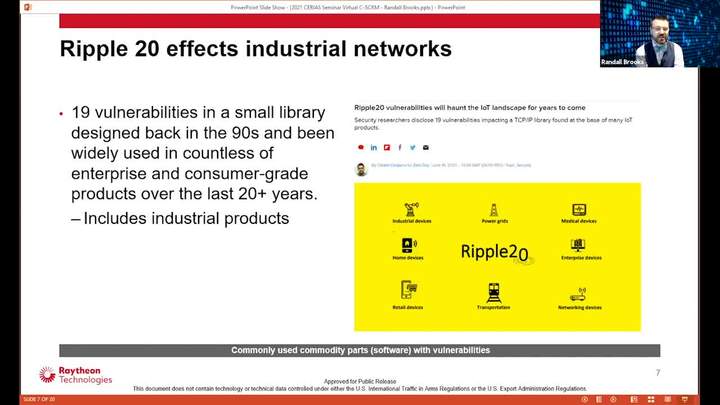
Cyber Supply Chain Risk Management (SCRM) and its impact on information and Operational Technology (IT/OT)
Randall Brooks - Raytheon

Technology, Self-Determination, and the Future of the Future
Cory Doctorow - Electronic Frontier Foundation
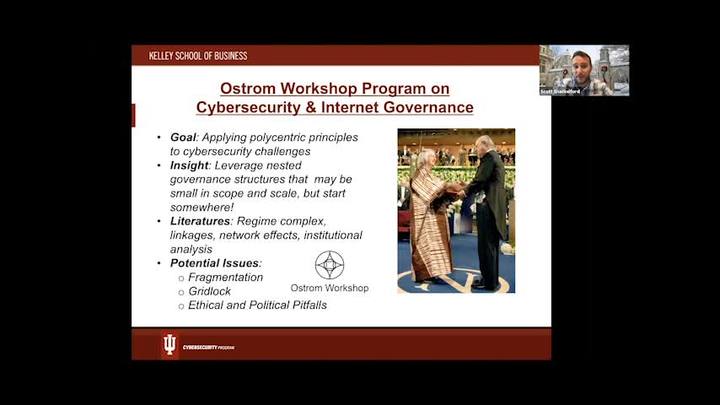
The Internet of Things: What Everyone Needs to Know
Scott Shackelford - Indiana University

Building Practical Security Systems for the Post-App Smart Home
Adwait Nadkarni - College of William and Mary

Maximizing Cyber Deception to Improve Security: An Empirical Analysis
Kimberly Ferguson-Walter - Laboratory for Advanced Cybersecurity Research, NSA Research

Improving the Accuracy of Blocklists by Aggregation and Address Reuse Detection
Sivaram Ramanathan - University of Southern California

Results from the Field: Cybersecurity in Nonprofits and Why it Matters
Kelley Misata - Sightline Security

NUTS: eNcrypted Userdata Transit & Storage; Viewing Data as an Endpoint™ (DaaE) using Structured Cryptography
Yoon Auh - NUTS Technologies

The Pod People Campaign: Driving User Traffic via Social Networks
Courtney Falk - GoDaddy
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List