Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Showing: 76 to 100 of 931Affiliation shown is the affiliation at the time the talk was given.

Vulnerability Identification and Defense Construction in Cyber-Physical Systems
Khaled Serag
How the Cyberspace Domain has Changed the Game for the Space Domain
Scott Sage, Erin Miller

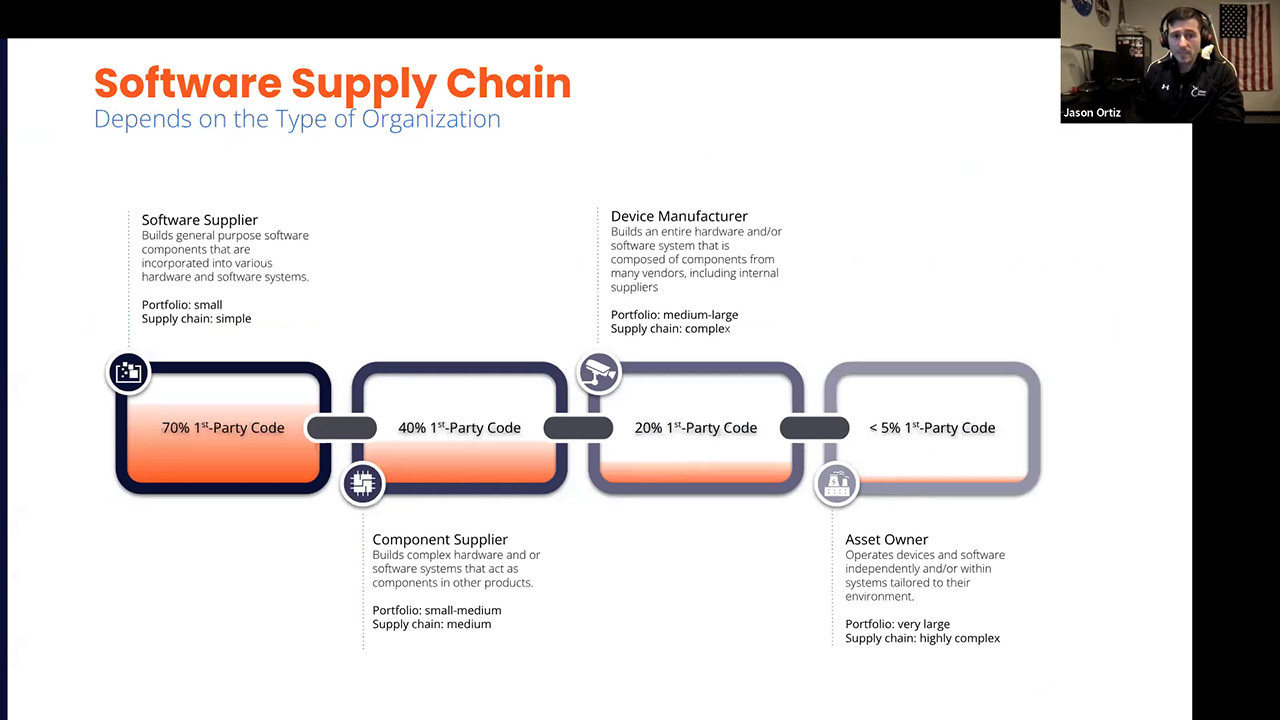
Enhancing Software Supply Chain Security in Distributed Systems
Christopher Nuland - Red Hat

Cyber defender's plead - If it's not codified – Please go away
Rita Foster - Idaho National Laboratory
From Compliance in the Classroom to Compliance on the Street, Important Lessons That Every Cybersecurity Professional Must Know
Jeremiah Sahlberg - Tevora
Cyber's Offspring: AI and the Missing Security Mindset
Chris Demchak - US Naval War College

Advancements and New Developments in Biometric Privacy, Security and Ethics
Marina Gavrilova - University of Calgary

Don't Copy That Floppy!: A History of Anti-cracking Controls in Early Video Games and Its Economic Impact
Kelly FitzGerald - Raytheon Technologies

Elements of Robust Real-Time Systems: Regularity-Based Virtualization and Functional Reactive Programming
Albert Cheng - University of Houston
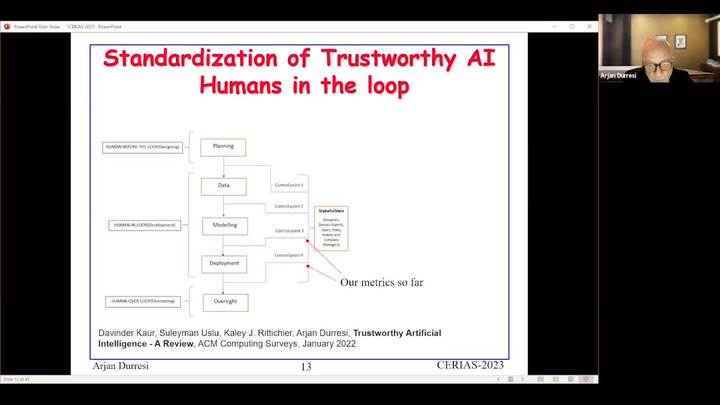
Trust Engineering – from Developing Resilient Systems to Artificial Conscience
Arjan Durresi - IUPUI
Chinese Views of Information and Future Warfare
Dean Cheng - Potomac Institute for Policy Studies

Problems and Challenges in Data Security Posture Management
Mummoorthy Murugesan - Normalyze, Inc.
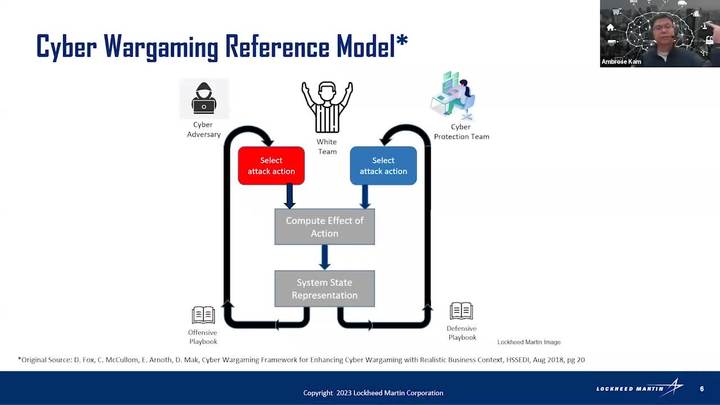
Applying Multi-Agent Reinforcement Learning (MARL) in a Cyber Wargame Engine
Ambrose Kam - Lockheed Martin
Users Are Not Stupid: Six Cybersecurity Pitfalls Overturned
Julie Haney - National Institute of Standards and Technologies

Fast and Reliable Formal Verification of Smart Contracts with the Move Prover
Meng Xu - University of Waterloo

Making Cybersecurity Reliable and Cybersecurity Careers Rewarding
Brian Barnier & Prachee Kale - Think.Design.Cyber
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List