Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Showing: 176 to 200 of 931Affiliation shown is the affiliation at the time the talk was given.

From Machine Learning Threats to Machine Learning Protection Requirements
Michael Clark - Riverside Research
Authentication: Behind The Scenes When You Click "Check Out"
Warda Zahid Khan - Mastercard

Dramatically Reducing Attack Surface Using Integrity MAC Security Kernel
Roger Schell - AESec Corporation

From Compliance in the Classroom to Compliance on the Street, Important Lessons That Every Cybersecurity Professional Must Know
Jeremiah Sahlberg - Tevora

Flexible and Adaptive Malware Identification Using Techniques from Biology
Elena Peterson - Pacific Northwest National Laboratory

The Ghost in the Machine: Reconciling AI and Trust in the Connected World
Sam Curry and Alon Kaufman - Cybereason / Duality Technologies
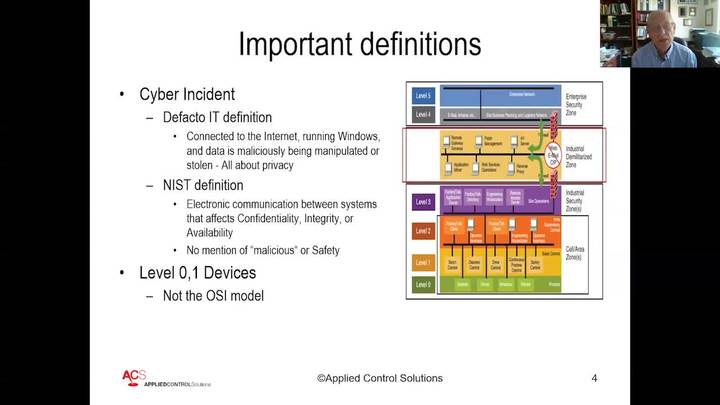
Cyber Security of Control Systems: The Second Coming of the Maginot Line
Joe Weiss - Applied Control Systems, LLC
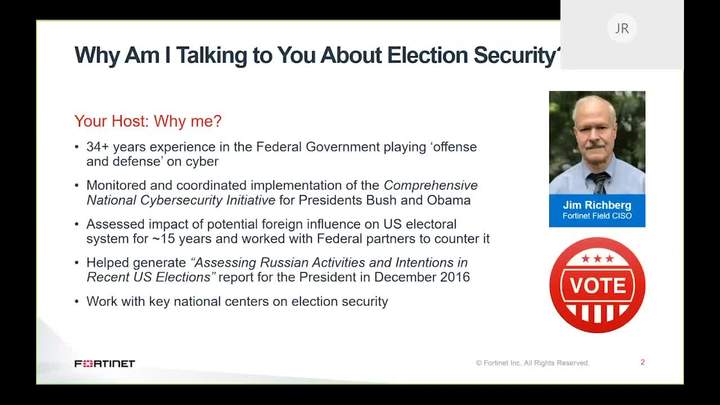
Election Security in the Age of COVID-19: Risk Management in the face of a "Perfect Storm"
Jim Richberg - Fortinet
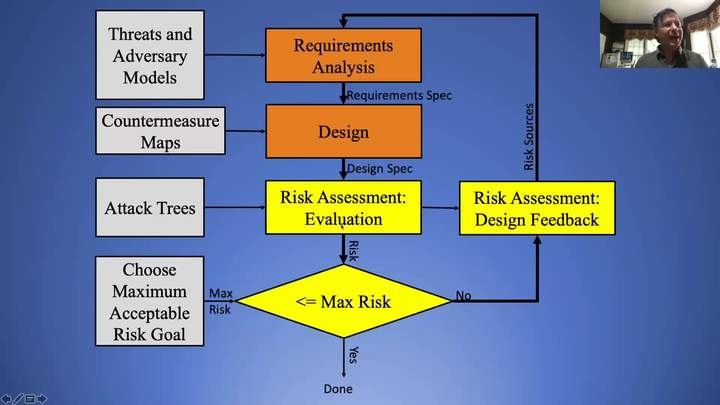
A Principled Approach to Cybersecurity Engineering
Sami Saydjari - Cyber Defense Agency, Inc.
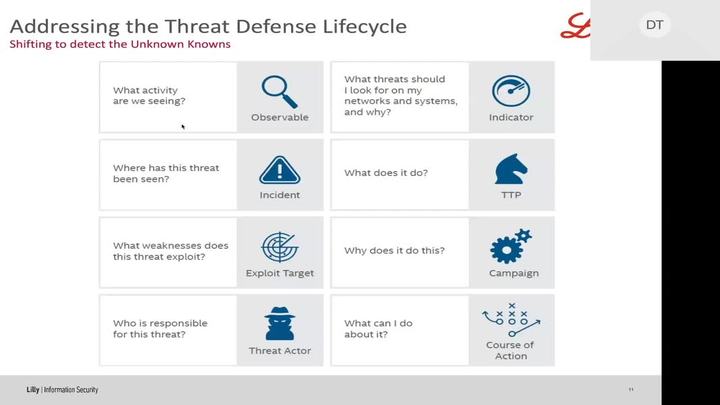
Proactive Endpoint and Network Security Operations. Detecting the Unknown Known
Corey Maypray - Eli Lilly
Public Sector Cyber Security 2020: Challenges and Rewards
Bruce Coffing - City of Chicago

Everyone Wants to Help You: Understanding the Issues and Surviving with a Multitude of Regulatory Authorities
Leon Ravenna - KAR Global

Security and Privacy of Connected Autonomous Vehicles
Vireshwar Kumar - Purdue University

Semantics-Driven, Learning-Based Privacy Discovery in Mobile Apps
Yuhong Nan - Purdue University
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List