Archive
2026 | 2025 | 2024 | 2023 | 2022 | 2021 | 2020 | 2019 | 2018 | 2017 | 2016 | 2015 | 2014 | 2013 | 2012 | 2011 | 2010 | 2009 | 2008 | 2007 | 2006 | 2005 | 2004 | 2003 | 2002 | 2001 | 2000 | 1999 | 1998 | 1997 | 1996 | 1995 | 1994 |
Results
Showing: 26 to 50 of 931Affiliation shown is the affiliation at the time the talk was given.

Annual CERIAS Security Symposium Closing Keynote IT, OT, IoT — It's Really Just the "T": An International and Historical Perspective
Michael Clothier - Northrop Grumman
What do we mean when we talk about AI Safety and Security?
Amir Sadovnik - Oak Ridge National Laboratory
Decrypting the Impact of Professional Certifications in Cybersecurity Careers
Hisham Zahid & David Haddad

Zero Trust Architectures and Digital Trust Frameworks: A Complementary or Contradictory Relationship?
Ali Al-Haj - Princess Sumaya University for Technology
Measuring Data Protection: A Causal Artificial Intelligence Modeling Approach
Robert Morton - Google Cloud
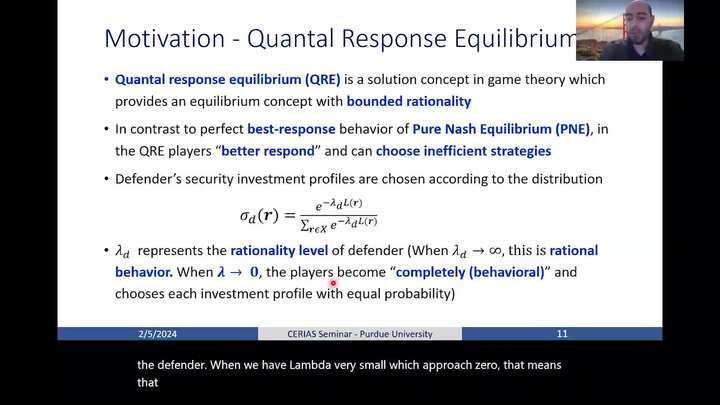
Effects of Behavioral Decision-Making in Proactive Security Frameworks in Networked Systems
Mustafa Abdallah - Purdue University in Indianapolis
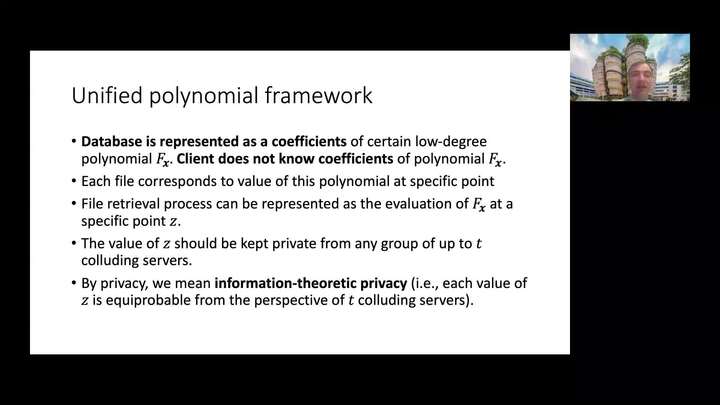
Querying Twice: How to Ensure We Obtain the Correct File in a Private Information Retrieval Protocol
Stanislav Kruglik - NTU Singapore

Fairness as Equal Concession: Critical Remarks on Fair AI
Christopher Yeomans - Purdue University

HomeRun: High-efficiency Oblivious Message Retrieval, Unrestricted
Yanxue Jia - Purdue University

The Road Towards Accurate, Scalable and Robust Graph-based Security Analytics: Where Are We Now?
Zhou Li - University of California, Irvine

Dissecting the Software Supply Chain of Modern Industrial Control Systems
Michail Maniatakos - NYU Abu Dhabi

Shamrock Cyber – When Luck Just Isn't Enough
Chance Younkin - Pacific Northwest National Laboratory

Exploiting Vulnerabilities in AI-Enabled UAV: Attacks and Defense Mechanisms
Ashok Vardhan Raja - Purdue University Northwest

IDART (Information Design Assurance Red Team): A Red Team Assessment Methodology
Russel Waymire - Sandia

Empowering the Next Generation of Digital Defenders: Ethics in Cybersecurity and Emerging Technologies
Chris Kubecka de Medina - HypaSec

AI's Security Maze: Navigating AI's Top Cybersecurity Risks Through Strategic Planning and Resilient Operations
David Haddad - Purdue University
Ways to Watch

Watch Now!
Over 500 videos of our weekly seminar and symposia keynotes are available on our YouTube Channel. Also check out Spaf's YouTube Channel. Subscribe today!- Upcoming
- Past Seminars
- Previous Speakers
- Open Dates (Fall/Spring)
- Attending the Seminar
- About the Weekly Seminar
- CPE Credit Information (PDF)
- Join our Mailing List